Recently, cybersecurity researchers have uncovered a critical command injection vulnerability affecting approximately 92,000 D-Link Network Attached Storage (NAS) devices. This flaw poses a significant security risk as it allows threat actors to execute arbitrary commands remotely, potentially compromising the integrity and confidentiality of stored data.
The vulnerability stems from a flaw in the D-Link DNS-320L, DNS-320LW, DNS-327L, DNS-345, and DNR-322L NAS devices’ firmware. These devices are widely used by individuals and businesses alike for storing and accessing files over a network.
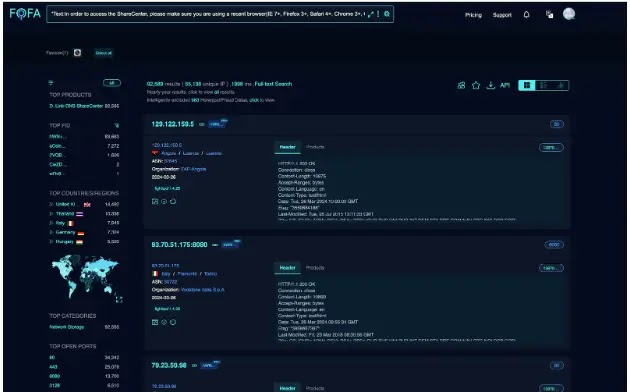
This exists in the nas_sharing.cgi file of these devices and the command injection vulnerability (CVE-2024-3273) exists in the system parameter.
As a matter of fact, these vulnerabilities affect more than 92,000 D-Link NAS devices that are exposed over the internet.
However, patches for these vulnerabilities have been published by D-Link and users are encouraged to patch them as soon as possible.
Vulnerability Details
According to the reports shared, if these vulnerabilities are subjected to exploitation, it could allow a threat actor to perform an arbitrary command execution on the affected device and gain access to sensitive information.
Additionally, a threat actor could also potentially perform a system configuration alteration or denial of service by specifying a command via the command parameter.
The nas_sharing.cgi is a CGI (Common Gateway Interface) script that has a hardcoded account that could be used as a backdoor through username and password exposure.
The exploitation is very simple as the parameter request includes a username (user=messagebus) and an empty password (passwd=). This could provide unauthorized access for threat actors without any proper authentication.
Further, command injection can be performed through the System parameter, which carries a base64-encoded value that, when encoded, becomes a command.
Exploitation
A threat actor can craft a malicious HTTP request targeting the /cgi-bin/nas_sharing to exploit this vulnerability.cgi endpoint.
The resulting response of this HTTP request contains the decoded system parameter value sent in the request.

Affected Products
- DNS-320L Version 1.11, Version 1.03.0904.2013, Version 1.01.0702.2013
- DNS-325 Version 1.01
- DNS-327L Version 1.09, Version 1.00.0409.2013
- DNS-340L Version 1.08
Users of these products are recommended to upgrade to the latest versions in order to prevent the exploitation of these vulnerabilities by threat actors.


